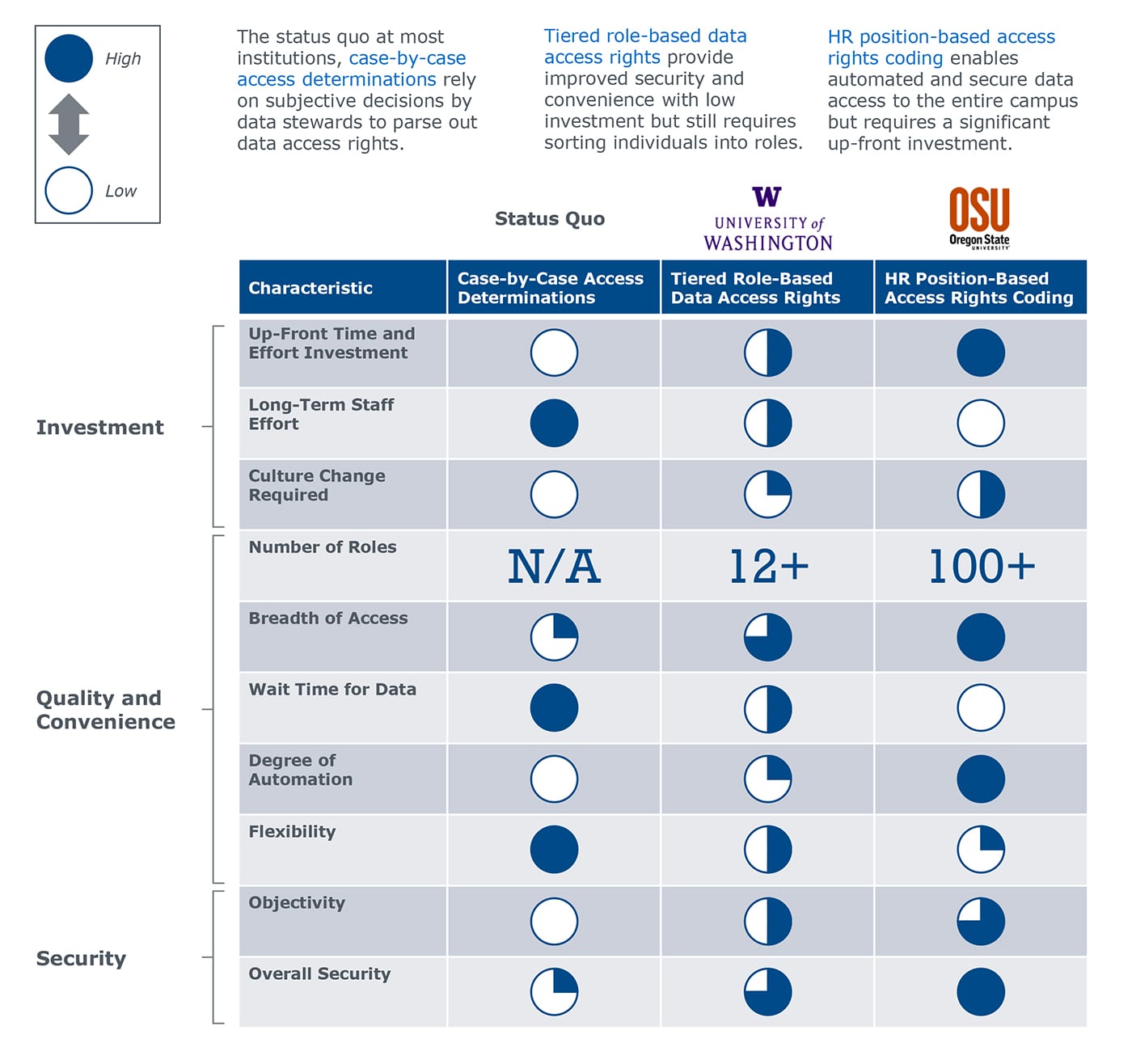
Is a role-based data access model right for your institution?
No access model is perfect, but role-based methods provide improved speed to data, reduced long-term staffing costs, and enhanced security as compared to case-by-case access determinations.
Determining the right model for your institution requires careful considerations of investments, quality, convenience, and security. Based on our conversations with forward-thinking institutions regarding data access, here we compiled five key questions that you should consider when thinking about the access model your institution should implement:
1. To what degree do campus members consider themselves data stewards (open to data as an institutional resource) rather than data owners (possessive of their functional data)? Transitions to role-based data access models require campus members to consider themselves data stewards; if campus members consider themselves data owners, they will be less willing to provide open access to “their” data.
2. How often are campus members able to get the data they need for decision making when they need it? Often analyses require multiple steps. When campus members must make multiple requests to access data for a single analysis, the data-informed decision making process becomes prohibitively slow and tedious.
3. How much time do functional and IT staff spend on the administrative task of data request reviews and privilege changes? With a push at many institutions to become more data-informed, the demand for data across campus will only grow. The number of requests for data access will grow accordingly, warranting automation of a low value-add task.
4. How soon after an employee leaves the institution are his or her data access privileges removed? Access to sensitive or confidential data creates an inherent security risk. At many institutions, staff maintain access to institutional systems and data repositories days or weeks after separation from the institution.
5. How well are you able to audit who has access to certain data sets across campus? For many institutions, distributed stakeholders grant data access subjectively, making access audits nearly impossible and further increasing institutional risk of improper data use.
Which access model is right for you?
Review a side-by-side comparison of different access models below to determine which is right for your institution.
More Blogs

How 76 data leaders are building better data governance

How can you tame data sprawl? Consider a chief data officer
