With classes online, now is the time to assess your campus’s cybersecurity practices
In the wake of COVID-19 sweeping across the nation, higher education CIOs have implemented business continuity plans and enacted remote teaching, learning, and staffing policies.
At the same time, IT security personnel will wait with bated breath for the first COVID-19 related cyberattack. Security professionals worry that remote learning has weakened higher education’s cybersecurity and will require campus unity to patch the security holes. The remote teaching and learning platforms were not built for total campus-wide use, and the transition’s speed forced circumvention of the institution’s security protocols, creating vulnerabilities. In the coming weeks, IT leadership will assess the level of COVID-19 security damage, but the assessment’s scale and detail depend on campus motivation.
Successfully running virtual higher education during the COVID-19 pandemic requires campus participation on all fronts. Therefore, IT security leadership must use this crisis as motivation for rallying campus to assess and improve cybersecurity practices. An admirable first step is monitoring peer institutions and the private sector for any COVID-19 related cyberattacks.
Concrete examples will ease the burden of motivating campus stakeholders in supporting a campus-wide security assessment. IT security leadership bears the responsibility to ensure that the campus understands potential security threats. In the past, EAB’s IT Forum profiled Ohio State University and how they successfully leveraged a security crisis to motivate their board into approving the security survey. The survey results educated department staff on the technical nature of cyber threats and the positive role that they can play in preventing and mitigating breaches. Ensure stakeholders have the information and tools to prevent another COVID-19 related incident.
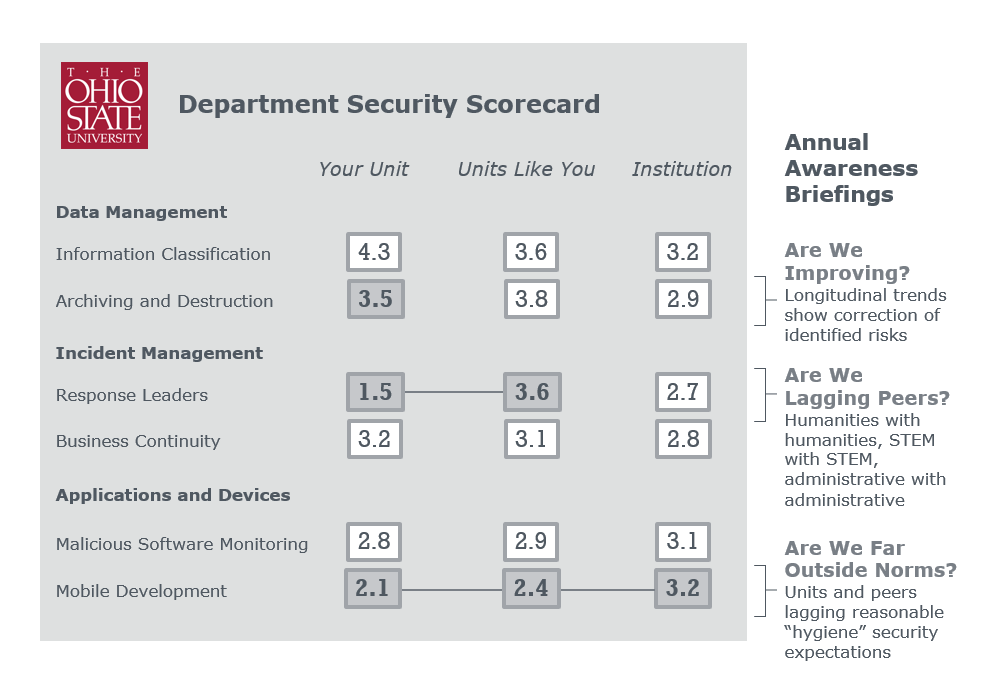
Ohio State’s campus security survey guided campus leaders
When the board of trustees at Ohio State University sought increased security reporting from IT, the CISO developed a simple self-grading survey mechanism for the campus. The survey was based on a standard National Institute of Standards and Technology (NIST) framework, with 100 questions developed in cooperation with campus experts (e.g., general counsel).
To maximize the impact of campus survey results and help individual units understand their vulnerability, the CISO produced department-level scorecards that compared units to their peers (e.g., academic departments, research centers) and the institution as a whole.
100%
The scorecards helped local academic and finance staff set benchmarks for improvement, understand peer comparisons, and identify key areas for remediation. Survey results were delivered and compiled through secure channels to remain confidential, as the results are sensitive information.
In its second year, the survey gained 100% participation from units, and instead of pushing units to accept cybersecurity policies, there was overwhelming department-initiated demand for CISO involvement with security consultation on asset tracking, policy writing, and vendor screening. Each unit maintained responsibility for configuring its security policies, but the department leaders began to understand that university-wide security was only as strong as the weakest department.
“We told units we couldn’t force them to participate in the surveys and scorecarding, but we’d report on who wasn’t participating to the trustees. No one wants to be the department in front of the board for not playing ball.”
– Helen Patton, CISO, Ohio State University
If you would like additional information and resources, members can access the IT Forum’s Elevating Security Awareness, Tool #5 “Department Security Scorecard Template“.
You may also like
More Blogs

How 76 data leaders are building better data governance

How can you tame data sprawl? Consider a chief data officer
