Why growing demand doesn’t guarantee success for cybersecurity programs
Cyberattacks and data breaches skyrocketed over the past two years-up 68% from 2020 to 2021 and another 14% from 2021 to 2022. Even top companies like Microsoft and Accenture remain vulnerable to attack. So, it should come as no surprise that national demand for cybersecurity master’s graduates has risen in response and is expected to grow across the coming decade.
However, even though the future looks bright, most cybersecurity programs will continue to fight for student interest and enrollment. While many university leaders express interest in launching cybersecurity master’s degrees, increasing competition and market concentration threaten all new programs’ ability to capture student attention.
To understand this complicated market and to help you decide if launching a master’s-level cybersecurity program is right for your school, my team and I analyzed the last five years of job postings, competitive landscape data, and employment projections. Here’s what you need to know about the master’s-level cybersecurity market.
Market demand suggests a promising future
Over the past two years, monthly employer demand for master’s-level cybersecurity professionals grew at almost 3% per month on average, greater than the average increase in demand for all master’s-level professionals at 1.74%.
Increase in job postings
7,000+
job postings per month have been available to master’s-level cybersecurity graduates for the past two years.The Grad Programs Presidents And Provosts Are Prioritizing
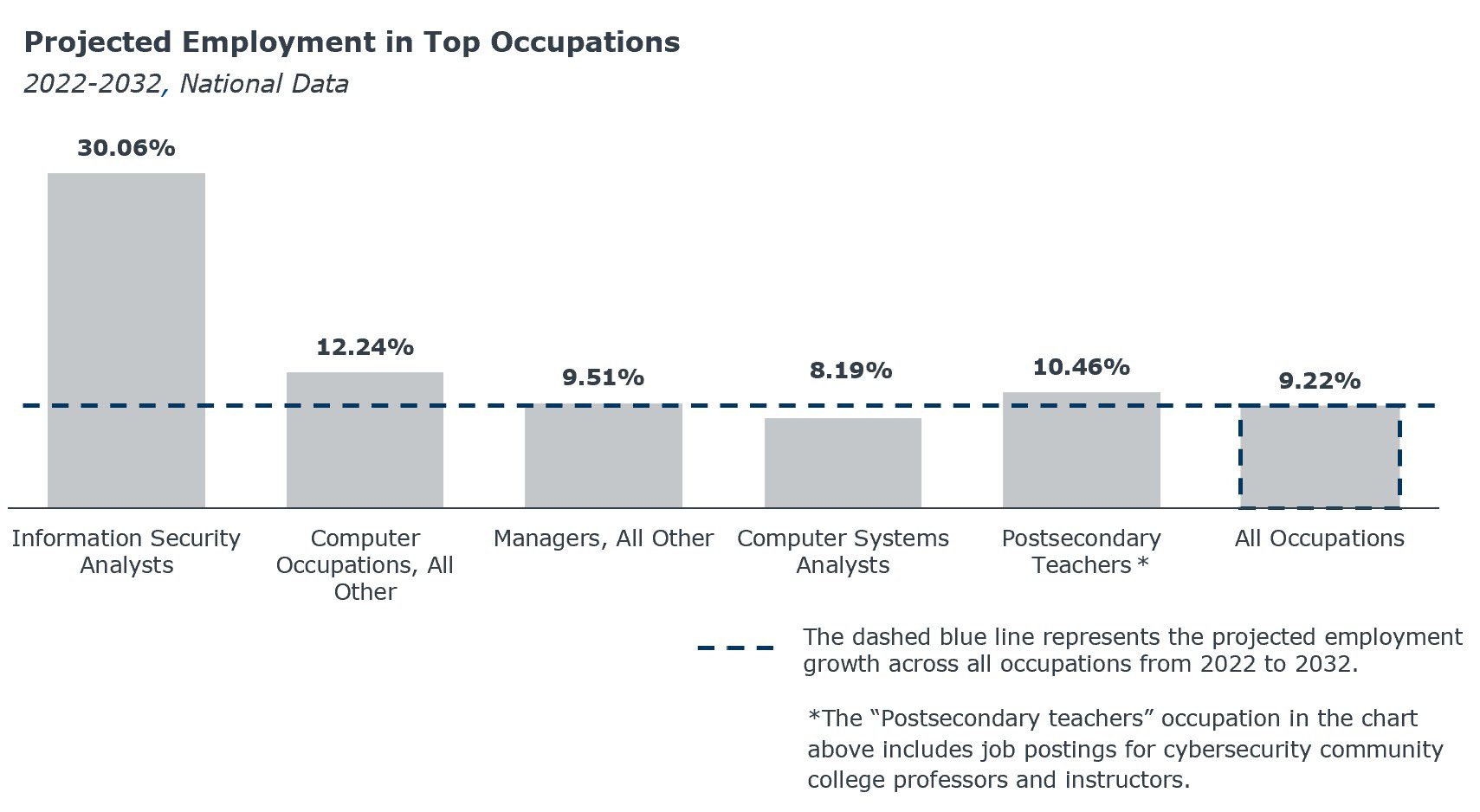
And we expect the demand for cybersecurity professionals to keep growing. Our analysis suggests employment opportunities for four of the five top related occupations will increase faster than average across the next 10 years. We expect job opportunities for the occupation most directly related to cybersecurity, Information Security Analyst, to grow over three times faster than the average.
Student interest mirrors this demand, as indicated by program completions. Annual program completions grew over 20% per year, on average, over the last five years. Likewise, total reported completions nearly doubled in the same period.
Market concentration, however, threatens most programs’ success
Master’s-level cybersecurity programs face a winner-take-all market, with the majority of graduates produced from a small minority of programs. The University of Maryland Global Campus and Western Governors University produced almost 30% of all 2020-2021 cybersecurity master’s program graduates. While the median program size increased by four completions over the analyzed period, this is still relatively minimal considering the top 10 programs from 2020-2021 each grew an average of 165 completions.
Does Your Program Design Support Enrollment Growth?
This market concentration likely outweighs the positive market signals outlined above for most schools. Especially when we know large online schools dramatically outspend most schools on marketing – Western Governors, for example, reportedly spent $127M on advertising and promotion in 2020. Our advice: find less concentrated market opportunities if you’re seeking enrollment and/or revenue growth.
Considerations for a successful cybersecurity program
Our Professional and Adult Education Forum researchers also analyzed top programs’ structure and curriculum to identify what you would need to offer to compete. It all comes down to speed-to-completion, program flexibility, and return on student investment.
Here’s What Graduate Students Are Looking For, In Their Own Words
Time to completion: As enrollment leaders know, adult learners prefer short times-to-completion and high program flexibility so they can achieve their goals quickly. These factors often lead most potential students to consider the online giants. To best meet potential students’ needs and align with competition, require no more than 36 credits and limit expected completion time to 24 months or less to attract adult learners eager to complete their education quickly.
Modality: Deliver courses online to meet students’ expectations for maximum convenience and to reach the largest possible audience. All of the largest programs offer either completely or mostly asynchronous online work. This asynchronous modality enables adult learners to balance their existing personal and professional obligations with their program requirements. Asynchronous, online programs also allow for a larger, more diverse applicant pool.
Cost: Estimated total cost varies more dramatically: for example, $17,180 at access-focused Western Governors University while $34,500 at selective George Washington University. Your program cost in terms of time, opportunity, and financial investment must be justified by the expected return – acquiring in-demand skills equips students to secure desired in-demand roles upon graduation.
Curriculum: Prioritize in-demand skills to best serve (and attract) potential students. Commonly taught in-demand skills at top programs include familiarity with IT infrastructure and an ability to audit its security and vulnerability. Rarely taught in-demand skills include programming languages, especially Python, and other technical skills like ethical hacking. If these skills lie outside of your program’s scope, consider creating pre-program coursework or an add-on certificate (e.g., UMGC’s graduate certificate in systems engineering) to supply graduates with these in-demand skills. See our analysis of fundamental and emerging skills below for more in-demand skills to consider.
Differentiators: Finally, highlight your program’s differentiators to capture student attention. Lower cost, greater flexibility, local partnerships, and/or greater emphasis on student support and connection can distinguish your programs from competitors. See below for some examples of “stand-out” program features.
Top skills taught in relevant job postings
| Fundamental Skills* | Emerging Skills |
| Computer Science | Information Assurance |
| Certified Information Systems Security Professional | Software Engineering |
| Auditing | Computer Networks |
| Information Systems | Penetration Testing |
| Vulnerability | Python and Java |
| Automation | Cloud Computing Security |
| Risk Analysis | Encryption |
“Stand Out” Program Features
In-demand Concentrations: Wilmington University’s Master of Science in Cybersecurity offers program concentrations in Cyber-terrorism and SCADA Cybersecurity systems. While profiled schools infrequently offer concentrations, today’s adult learners find this personalization option attractive.
Embedded Industry Certifications: Western Governors University’s Online Master’s in Cybersecurity and Information Assurance builds two EC-Council certifications into their program. The exam costs are included in students’ tuition and fees. Industry certifications allow students to demonstrate technical skills to employers.
Options for Accelerated Learning: Purdue University Global’s Master of Science in Cybersecurity Management offers an accelerated program track (ExcelTrack™). This option utilizes competency-based education (CBE) to prioritize flexibility and individualization. To see if CBE is right for your students and program, see EAB’s CBE resources here.
Launching any new master’s program comes with risks and the market for a master’s-level cybersecurity program is riskier than most. Whether or not your school decides to venture into this market, EAB still has resources to help you both understand your larger enrollment opportunities as well as ensure you’re well-equipped to recruit students to your offerings. Check out our resources below for more on graduate markets:
- EAB’s Enrollment Growth Strategy Resource Center offers helpful tools and insights into the grad market.
- Watch our recent webinar about the ways presidents, provosts, and VPEMs are prioritizing graduate and adult learner enrollment.
Lastly, if this has also gotten you thinking about your own cyber-vulnerability, use our Cybersecurity Diagnostic to evaluate the strength of your own school’s cybersecurity strength.

More Blogs

The big bets that actually drive online enrollment growth

How to use state demand data to launch or revitalize programs

Meeting the Gen Z moment
Great to see you today! What can I do for you?